Describe Physical Security Methods in Use

Things To Check Before Hiring A Security Guard Security Guard Security Guard Services Guard


Threat Modeling 12 Available Methods

It Risk Assessment Template Elegant Amelia O Callaghan A2 Blog Risk Assessment Form Ing Thank You Card Wording Statement Template Assessment Tools

Arc Industrial Cybersecurity Maturity Model Icmm Jpg Cyber Security Surveys Solutions

Handbook On The Design Of Physical Protection Systems For Nuclear Material And Nuclear Facilities Iaea

To Use The Right Methods For Updating The Marketing Strategy Marketing Strategy The Marketing Marketing

Technology Scientific Investigation Technology Quantum Computer

Access Control System What Is It Nedap Security Management

Confidence And Security Building Measures Communication Relationship Confidence Building Confidence
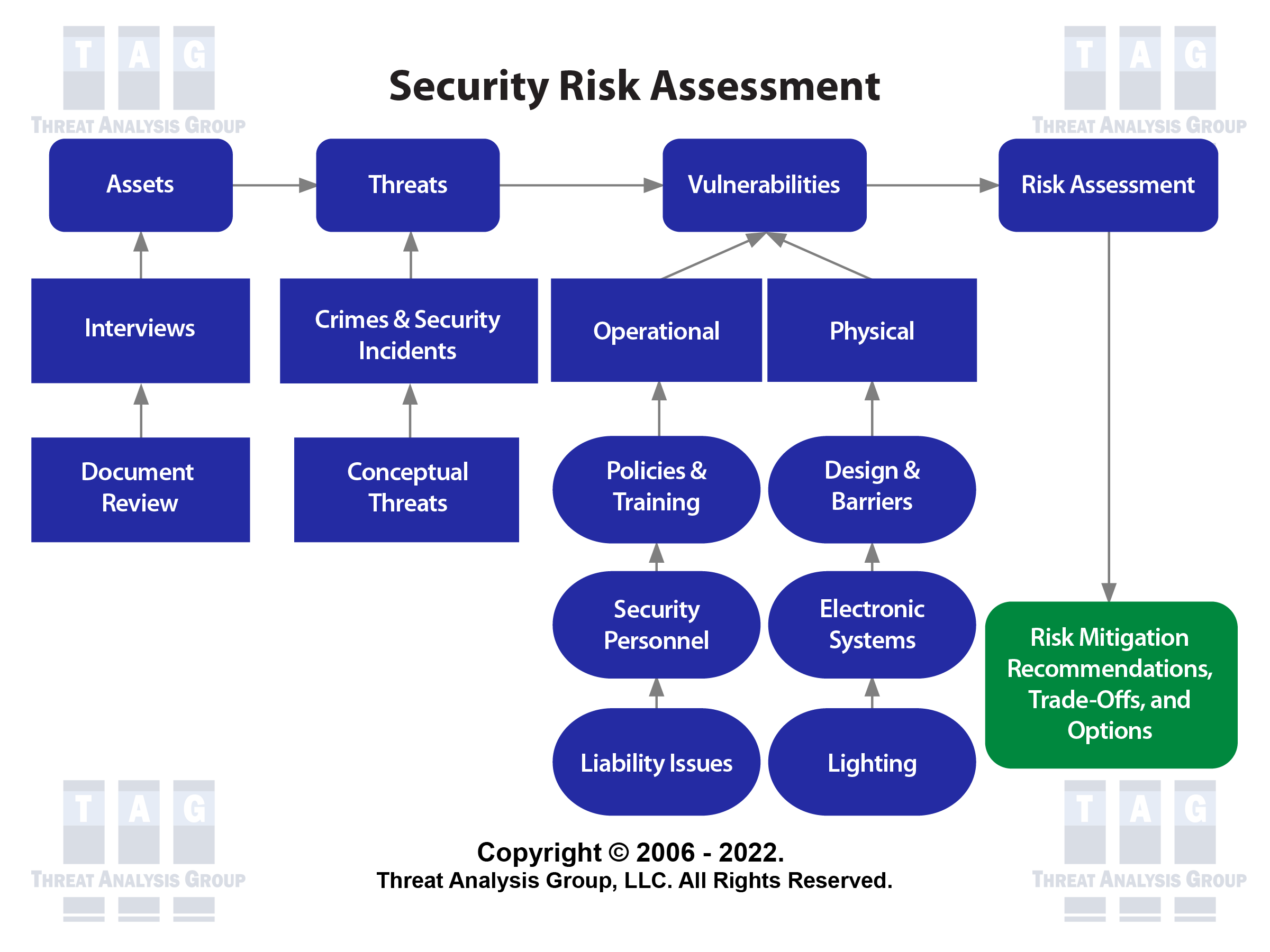
Security Risk Management Threat Analysis Group

10 Golden Rules Of Security And Safety Bureau Biosecurity

The 8 Levels Of It Security In The Data Center Computer Technology Information Technology Computer Security

The Modern Research Data Portal Science Intense Data

Lockpicking Detail Overkill Lock Security Device Electrical Connector Security Device Skills To Learn Improvisation

Cyber Assurance Of Physical Security Systems Cpni

Access Control System What Is It Nedap Security Management

Now Publishers Cyber Physical Threat Intelligence For Critical Infrastructures Security Securing Critical Infrastructures In Air Transport Water Gas Healthcare Finance And Industry

From Wikiwand Database Data Modeling Distributed Computing Database

I Recently Saw A Post That Used An Iceberg To Describe A Concept And It Struck Me How This Same Analogy Could Be Used To Describe Roadmap Management Analogy
